Blog
Scan a website for malicious URLs with AsyncURLCrawler and VirusTotal

A malicious URL is a hyperlink with the intent of facilitating scams, attacks, and fraud. Clicking on such URLs may result in the downloading of ransomware, exposure to phishing or spearphishing emails, or engagement in various forms of cybercrime. In this blog post a method is presented to extract URLs inside a website and scan them automatically using VirusTotal.... [Click for more]
Security Vulnerability Scanning in CI/CD Pipelines
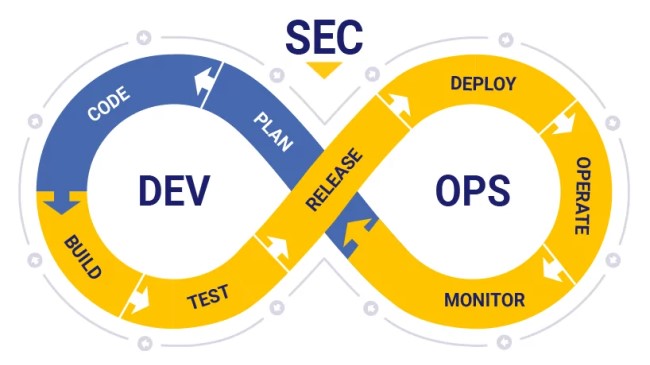
A security vulnerability represents a system weakness that, if exploited, can lead to unauthorized access to confidential data, violate data integrity, or result in denial of service. It is necessary to proactively identify and mitigate vulnerabilities prior to deployment into the production environment. Automated scanning processes integrated into the CI/CD pipeline play a pivotal role in achieving this goal. Automating these scanning tasks enhances efficiency and ensures that potential vulnerabilities are detected and mitigated early in the development lifecycle, minimizing the risk of security breaches. This approach is called DevSecOps... [Click for more]
Design Considerations to Develop a Robust System Against DDoS Attacks
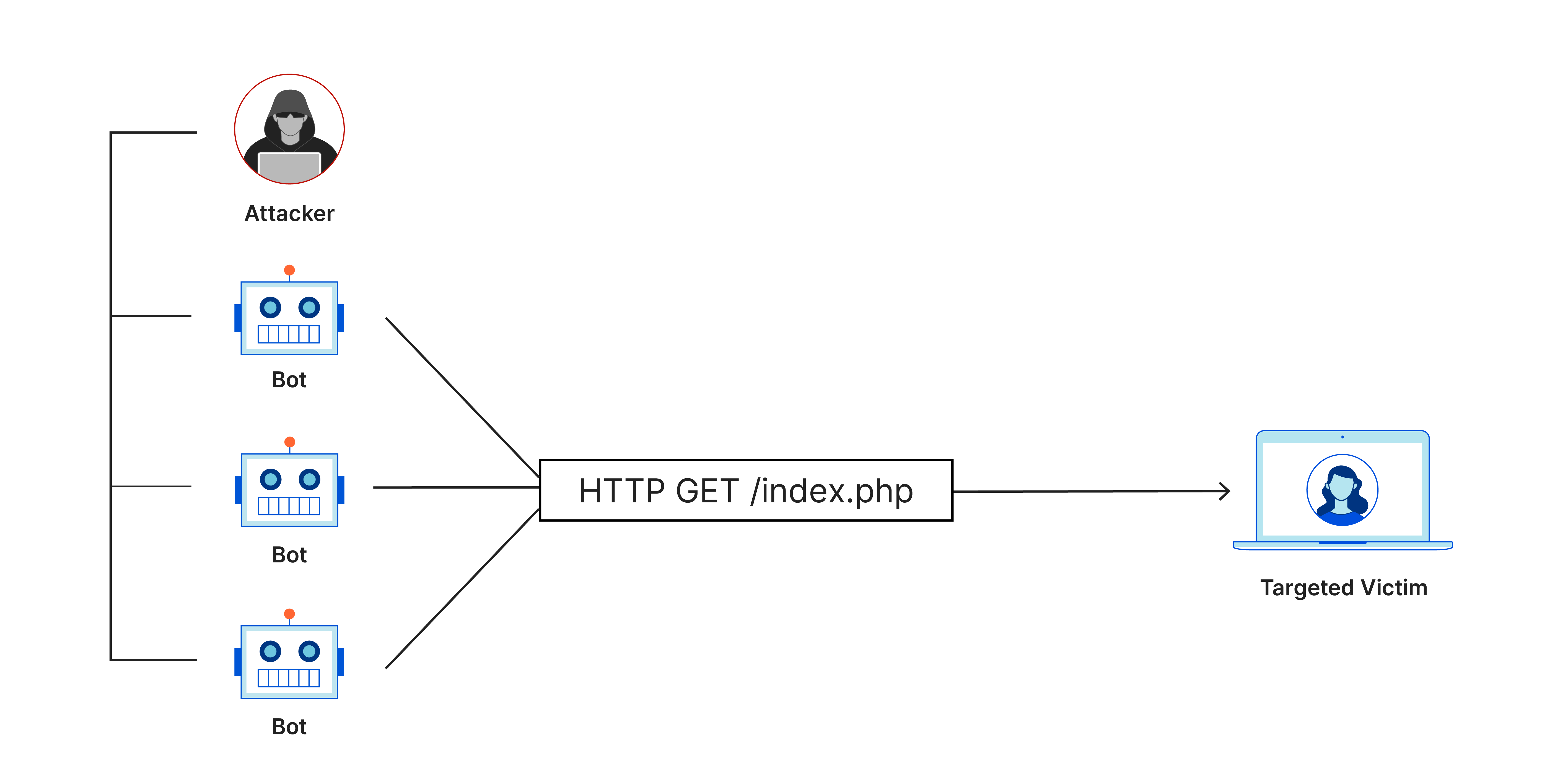
A DDoS (Distributed Denial of Service) attack aims to disrupt a service by flooding it with huge amounts of traffic, exhausting its resources. DDoS attacks have the capability to overwhelm nearly any online service. Despite advanced tools for detection and mitigation, DDoS attacks remain a persistent challenge, evolving like a cat-and-mouse game. While ML-based Intrusion Detection Systems (IDS) are effective, a comprehensive approach is crucial due to the dynamic cyber threat landscape. Neglecting fundamental system design principles can expose a system to DDoS vulnerabilities. I’ve examined key design considerations to address this issue for software engineers in this blog post ... [Click for more]
Git: Less commonly used but handy commands

Git is a daily tool for developers, offering a wide range of commands. This post doesn’t aim to introduce basic git commands or delve into its internals. Instead, it draws from my experience to highlight some handy yet less commonly used git commands. Let’s make it short and begin ... [Click for more]
A Cryptographic Client Side State
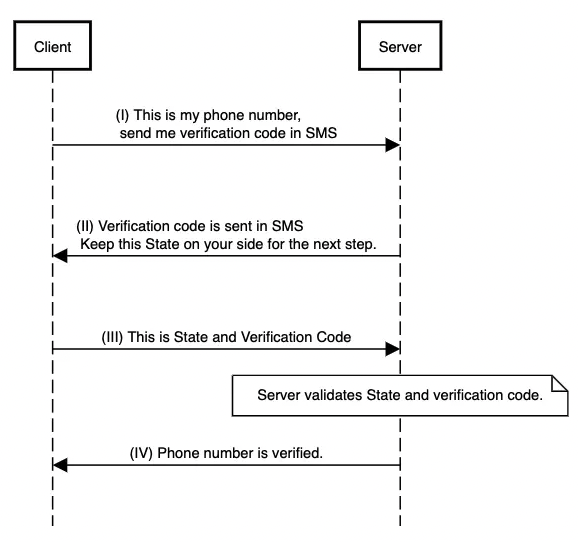
In web applications, sometimes it is needed to exchange multiple messages between server and client to complete a user journey. For example, this is a popular flow in user phone number verification:
- User enters phone number.
- User gets verification code in SMS.
- User enters received verification code.
- Now, user’s phone number is verified.
Rate Limiter with Redis

Rate Limiter, controls and limits the rate of requests to access an object or resource. This limitation is mostly represented by units like Requests Per Seconds (RPS) or Requests Per Minutes (RPM). The reason to use Rate Limiter is to maintain the resources available and prevent denial of service (DoS). One of the common algorithms to implement Rate Limiter is Leaky Bucket. In this blog post, the Leaky Bucket is implemented based on Redis cache engine. ... [Click for more]